The proliferation of drones in modern warfare has transformed military operations, providing unmatched capabilities in surveillance, reconnaissance, and targeted strikes. However, integrating drones into military strategies has revealed significant vulnerabilities, including risks associated with switching and hijacking drone feed, and its intelligence leakage. Recent incidents in the Ukraine-Russia conflict have demonstrated the dangers of compromised drone feeds, emphasising the urgent need to address these challenges. For India, navigating complex geopolitical dynamics and external threats, the critical question is: Should the Indian defence industry focus on technologies that enable and counter drone-feed hijacking?
Emerging drone technologies are particularly susceptible to attacks targeting the safety and security of data, infrastructure, and public safety. Exploiting zero-day vulnerabilities and security gaps, attackers can infiltrate drone communication networks, posing serious threats to operational integrity.
The vulnerabilities of communication mediums and frequency-based systems further heighten the risks of attacks. Modern drones, equipped with cameras and GPS signals, are especially at risk, necessitating robust cybersecurity measures. This article examines the implications of drone-feed switching and hijacking, explores the potential for weaponising these capabilities, and highlights the strategic imperative for the Indian defence industry to prioritise innovations in drone cybersecurity and counter-drone technologies to secure its military assets and maintain operational superiority.
The Reality of Drone Feed Switching in Warfare
Drones have become indispensable in modern applications, from military operations to civilian uses, but their reliance on communication networks and sophisticated technologies introduces significant vulnerabilities. These include drone feed switching, RF jamming, GPS spoofing, software-based attacks, and hardware manipulation. The following sections detail these vulnerabilities, their methods of exploitation, and potential countermeasures.
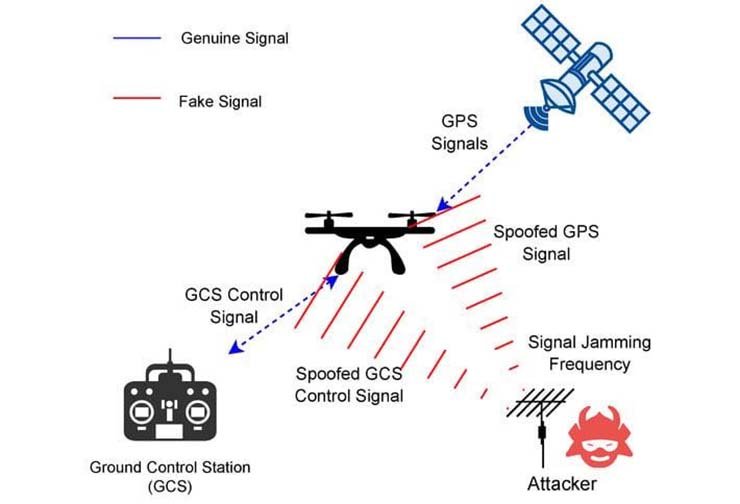
Drone feed switching involves intercepting and manipulating live video or data streams between drones and their ground control stations (GCS). The enemy can misdirect drones, gain sensitive intelligence, or disrupt operations by exploiting the vulnerabilities in GPS-based frequencies, radio communication, and video transmissions. This poses severe risks such as operational disruptions, intelligence leaks, and psychological impacts, as evidenced during the Ukraine-Russia conflict.
Key Vulnerabilities in Drone Systems
(a) GPS Spoofing and Jamming
GPS signals, operating on bands like L1 (1575.42 MHz), L2 (1227.60 MHz), and L5 (1176.45 MHz), are crucial for drone navigation. These signals are weak and unencrypted, making them vulnerable to spoofing, where false signals mislead the drone about its location, and jamming, which disconnects the drone from authentic satellites. Anti-jamming antennas, encrypted GPS signals, and multi-GNSS receivers can mitigate these risks.
(b) RF Jamming
Drones operate on radio frequencies, typically in the 2.4 GHz to 5.8 GHz ISM bands, for command and control. Attackers use RF jammers to broadcast stronger signals on the same frequency, disrupting the communication between the drone and GCS. Countermeasures include frequency hopping protocols, AES-256 encryption, and directional antennas.
(c) Cloning
In physical environments, adversaries can capture drones, clone their hardware and software, and create replicas. Cloned drones can be used to eavesdrop on communications, launch attacks, or manipulate operations. Countermeasures include tamper-resistant hardware, behavioural monitoring, and remote attestation to verify the authenticity of drones.
(d) ESC-PWM Signal Attacks
Drones rely on electronic speed controllers (ESCs) connected via pulse width modulation (PWM) for motor control. By modifying ESC firmware or injecting malicious PWM signals, attackers can disrupt drone performance. Reliable firmware and intrusion detection systems are essential countermeasures.
(e) Software-Based Attacks
Tools like SkyGrabber exploit unencrypted communication links to intercept drone video feeds, stealing sensitive information. Attackers can monitor or manipulate these feeds for operational disruption. Using secure communication protocols such as Secure Real-Time Transport Protocol (SRTP) and encrypting data streams can prevent such breaches.
(f) SDR Attacks
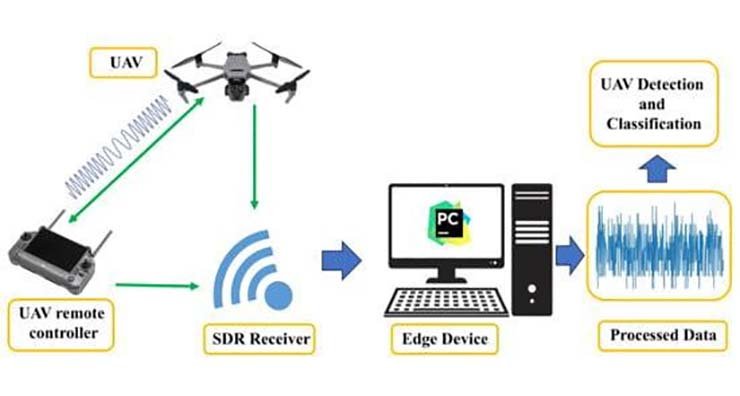
Software-defined radios (SDRs), such as RTL-SDR, allow attackers to eavesdrop on drone communications. Operating in ranges from 25 MHz to 1.75 GHz, they tune to drone frequencies to intercept or manipulate information. Devices like HackRF extend this capability to transmit messages. Countermeasures include encrypted communication and frequency-hopping techniques.
(g) Denial of Service (DoS) Attacks
Small drones with limited computational power are vulnerable to DoS attacks, where attackers flood the system with random commands, disrupting operations. Ensuring robust data links and resilient software can help counter these attacks.
(h) De-authentication Attacks
De-authentication attacks target drones operating via WiFi, exploiting vulnerabilities in network protocols to disconnect them. Tools like Aircracking and ESP8266 can execute such attacks. Encrypting WiFi signals and adopting robust password policies are effective deterrents.
(i) Man-in-the-Middle (MITM) Attacks
MITM attacks allow adversaries to intercept, alter, or inject traffic in real time, compromising drone communications. For instance, attackers have exploited XBee chips by modifying internal parameters. Encrypting data and authenticating communication streams are critical for prevention.
(j) Sensor-Based Attacks
UAV sensors for GPS, infrared, and radar can be manipulated through false data inputs or electromagnetic interference. Directed energy attacks exploit vulnerabilities across the electromagnetic spectrum. Secure sensor communication and misbehavior detection mechanisms can enhance resilience.
The Emerging Threat of Drone Hijacking
Drone feed-switching often signals a greater danger: drone hijacking. By compromising the communication link, adversaries can take control of drones to perform reconnaissance for their own purposes, redirect payloads (including munitions) towards friendly forces or civilian areas, or destroy and disable the drone to deny its use to the original operator. As electronic warfare and cyber capabilities advance, the threat of drone hijacking is becoming increasingly real. This potential for weaponisation raises urgent concerns about the readiness of military forces to address such scenarios effectively.
Drone feed switching involves intercepting and manipulating live video or data streams between drones and their ground control stations (GCS). The enemy can misdirect drones, gain sensitive intelligence, or disrupt operations by exploiting the vulnerabilities in GPS-based frequencies, radio communication, and video transmissions
Global Perspectives on Drone Security
Globally, the vulnerabilities in drone operations have prompted nations to prioritise the development of counter-drone technologies. The United States invests significantly in electronic warfare systems designed to jam or spoof drone communications, with initiatives like DARPA’s ‘Gremlin’ programme focusing on swarming drones with robust security features. Israel, renowned for its advanced drone technology, has developed systems such as the Iron Dome to intercept hostile drones and secure communication feeds. China, as a leading producer of commercial and military drones, emphasises cybersecurity enhancements and counter-drone solutions to maintain its operational edge. Russia, leveraging its expertise in electronic warfare, has showcased its ability to disrupt drone operations, notably using the Krasukha-4 system during the Ukraine conflict.

India’s Strategic Imperative in Drone Warfare
As drones increasingly define modern military operations, India must adopt a dual-pronged strategy to secure its indigenous systems and develop offensive capabilities to counter adversaries effectively. Given the evolving global security landscape and India’s geopolitical challenges, this approach is vital to maintaining a strategic edge in drone warfare.
- Securing Indigenous Drone Systems
India has made notable advancements in indigenous drone development, exemplified by projects such as the Rustom-II UAV and SWiFT (Stealth Wing Flying Testbed). Additionally, Indian industrial players are contributing significantly to developing micro-to-medium AUW drones using ISM band technologies. However, ensuring the security of these systems is critical for their operational effectiveness. Relying on indigenously developed drone components ensures that the architecture (both hardware and software) remains confined to trusted entities, minimising the risk of adversaries exploiting vulnerabilities or hacking into the systems. This approach provides India with greater control over the entire lifecycle of its drones, from design and development to deployment and maintenance, while reducing dependency on foreign suppliers. By prioritising home grown technology, India not only strengthens its drone security and resilience but also reinforces its technological sovereignty, ensuring operational preparedness in the rapidly evolving domain of drone warfare.

Indigenous development also enables the integration of advanced security measures, such as AES-256 or quantum encryption, to protect communication links and prevent sensitive data interception. Techniques like Frequency Hopping Spread Spectrum (FHSS) enhance resilience against jamming and feed switching, especially in critical regions like the Line of Actual Control (LAC). Real-time AI-driven anomaly detection further strengthens cybersecurity, safeguarding drones deployed in sensitive areas like Kashmir. Additionally, fortifying ground control stations (GCS) against physical and cyber intrusions is vital to preventing operational breaches. Past incidents, such as the drone interception attempts during the Balakot airstrikes, underscore the necessity of robust GCS security.
- Developing Offensive Counter-Drone Capabilities
There is a requirement for investments in technologies to effectively neutralise adversarial drones, given their increasing use by neighbouring states and non-state actors. The frequent spotting of foreign-origin drones dropping arms in Punjab underscores the urgency of this need. Advanced signal interception systems, such as software-defined radios (SDRs) and electronic warfare tools, can enable the covert interception of enemy drone communications — an area where limitations during the Kargil conflict highlighted critical gaps. Command injection technologies, which allow for overriding enemy commands to assume control, could prove invaluable in neutralising hostile drones, particularly those deployed by insurgents in sensitive regions like Jammu and Kashmir. Additionally, localised electromagnetic pulse (EMP) weapons, inspired by systems like the U.S.’s THOR (Tactical High Power Operational Responder), can disable drones within a defined range without physical contact. Integrating such EMP capabilities into India’s border defence strategies along the western and northern frontiers would significantly mitigate the threat posed by adversarial drone swarms.

- Strategic Needs
- Cross-Border Threats: Drones carrying weapons and contraband have been a recurring issue along the India-Pakistan border. Strengthening counter-drone capabilities through signal interception and EMP weapons could help address these threats effectively.
- Global Benchmarking: Nations like the United States and Israel are already deploying advanced counter-drone technologies. For instance, Israel’s Drone Dome system intercepts and neutralises hostile drones using a combination of radar, jamming, and directed energy weapons. India could develop its own indigenous versions of such systems, like the DRDO’s anti-drone systems.
- Swarm Technology: With China’s demonstrated prowess in deploying drone swarms during military exercises, India must accelerate its own swarm drone programs, such as the DRDO’s ALFA-S project, to maintain regional parity.
Adversaries can capture drones, clone their hardware and software, and create replicas. Cloned drones can be used to eavesdrop on communications, launch attacks, or manipulate operations. Countermeasures include tamper-resistant hardware, behavioural monitoring, and remote attestation to verify the authenticity of drones
Future Technologies for Drone Security and Countermeasures
These next-generation technologies represent a significant leap forward in both the capabilities of drones and the measures required to counter potential threats. Their integration into defence strategies will enhance the effectiveness, security, and adaptability of unmanned aerial systems in increasingly complex operational environments.
(a) Quantum Encryption: Unbreakable Communication Links
Quantum encryption harnesses the principles of quantum mechanics to establish virtually unbreakable communication links. Unlike traditional encryption, which relies on mathematical algorithms, it employs quantum key distribution (QKD), where any interception or tampering disrupts the quantum state of particles, immediately alerting the system to a breach. This technology is pivotal in securing drone command-and-control links to prevent hijacking or spoofing by adversaries, safeguarding mission-critical data such as reconnaissance information from interception or decryption, and creating highly secure communication networks for coordinated drone operations in sensitive environments.
(b) Swarm Intelligence: Coordinated AI-Driven Drone Networks
Swarm intelligence uses AI algorithms to enable drones to operate collectively, mimicking the behavior of natural swarms like bees or birds. These systems can autonomously make real-time decisions, adapt to changing conditions, and coordinate their actions seamlessly. This technology has diverse applications, including deploying AI-driven swarms to surround, disable, or redirect hijacked enemy drones, enhancing defence against adversarial threats. In reconnaissance missions, drone swarms can efficiently cover vast areas, dynamically sharing data and adjusting their routes. Additionally, in disaster zones, swarms can collaborate to locate survivors, map damage, and deliver aid, leveraging their distributed intelligence for rapid and effective response.
- Directed Energy Weapons (DEWs): Non-Kinetic Drone Neutralisation
Directed energy weapons (DEWs), including high-energy lasers and microwave systems, are advanced tools designed to neutralise drones without physical contact. These systems work by overheating critical components or disrupting electronic systems, effectively disabling the targeted drones. They are particularly useful in neutralising unauthorised drones in restricted airspace without causing collateral damage, enhancing border security by preventing surveillance or attacks from enemy drones, and equipping mobile units with the capability to rapidly counter multiple drones in combat or urban scenarios.
- Blockchain for Data Integrity: Tamper-Proof Drone Feeds
Blockchain technology, renowned for its decentralised and secure ledger system, offers a powerful solution for ensuring the integrity of drone data streams. By recording every transaction on an immutable blockchain, any tampering or unauthorised access becomes immediately detectable. This technology ensures that real-time video feeds and telemetry data from drones remain authentic and untampered, provides transparent and tamper-proof audit trails for accountability and post-mission analysis, and enhances the resilience of drone operations by decentralising command systems to eliminate single points of failure.
Challenges and Strategies for Implementing Drone Hijacking Capabilities
While the potential benefits of drone hijacking technologies are significant, their development and deployment come with notable ethical, operational, and technical challenges. Ethically, employing such technologies raises complex questions about legality and morality, particularly in the context of international conflicts. Technologically, these capabilities require advanced electronic warfare systems and a deep understanding of diverse drone architectures, making their implementation highly complex. Operationally, offensive drone operations risk provoking retaliatory measures, potentially escalating conflicts. Furthermore, hijacked drones carry the inherent risk of malfunction or unintended collateral damage, complicating mission outcomes and undermining strategic objectives.
The vulnerabilities in drone operations have prompted nations to prioritise the development of counter-drone technologies. The United States invests significantly in electronic warfare systems designed to jam or spoof drone communications, with initiatives like DARPA’s ‘Gremlin’ programme focusing on swarming drones with robust security features
To address these challenges, a holistic approach integrating policy development, industry collaboration, and international partnerships is crucial. Clear policy frameworks must be established to regulate the use of drone hijacking technologies, ensuring a balance between leveraging offensive capabilities and adhering to ethical standards. Collaboration with private sector firms specialising in cybersecurity, artificial intelligence, and drone technology can drive innovation and enhance technical capabilities. Additionally, fostering international partnerships with allied nations will facilitate the sharing of best practices, the development of global standards, and coordinated efforts to counter common adversaries effectively. This multifaceted strategy can help mitigate the challenges while unlocking the potential of drone hijacking technologies for strategic advantage.
Drone forensics plays a vital role in addressing these risks, offering a systematic approach to identifying attacker objectives through the collection, preservation, and analysis of digital, software, and hardware evidence. This process not only aids in understanding the nature of attacks but also helps inform the development of new technologies and policies to mitigate similar threats in the future, thereby enhancing overall security levels.
Conclusion
The rise of drone feed switching and hijacking presents a significant challenge in modern warfare, with far-reaching implications for operational security, intelligence integrity, and strategic decision-making. For India, addressing these threats necessitates a proactive approach that combines securing indigenous systems with developing offensive counter-drone capabilities. By prioritising the security of domestically developed systems, investing in advanced technologies, and fostering collaborations with industry and international partners, India can enhance its operational readiness and safeguard its strategic interests. Aligning with global standards and accelerating domestic innovation will not only strengthen India’s drone operations but also position the country as a leader in the evolving domain of drone warfare. These measures will ensure India’s ability to counter emerging threats effectively while maintaining a decisive edge in an increasingly contested battlespace.
–The writer is an SME and independent consultant in military technology. The views expressed are of the writer and do not necessarily reflect the views of Raksha Anirveda






